As my text says, I am referring to the Updater that was pulled for instability. Not the firmware itself. Once that is successfully installed on your device the method by which it was installed should not matter.
And actually, the OS is barely involved. The LVFS and Windows updates for Intel FWs use Capsule-Updates wherever possible. That means the OS just forwards the firmware files to the BIOS and the BIOS decides what to do with them, namely updating itself. If you have a capsule, it should work the same on Windows or Linux, because the same BIOS takes over after the required reboot. And both Windows and Linux do not have to do much themselves.
Problem is only, that Framework is apparently not setup to update ME firmware from a capsule (other manufacturers have that), so they need, in addition to the capsules, a manual updater from Intel (FWUpdLcl) for that, and that will be OS specific and according to Framework only exists as EFI executable and Windows executable, not for Linux.
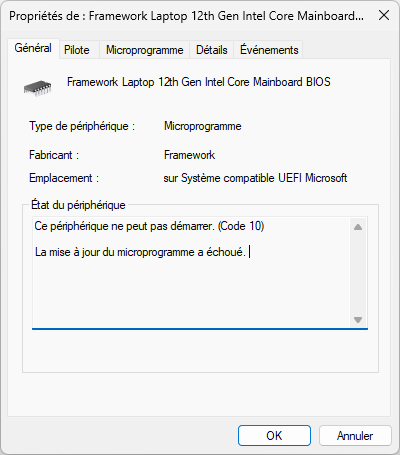
The EFI-Updater does not seem to use the Capsule-method, but Insyde’s updater-executable (H2OFFT, that is also used for the AMD-systems for the Windows updates, but also only seems to exist as EFI or Windows executable). That gives it greater control. And in this specific case means it logs its outputs to the screen, so you can see what is being updated and why it fails, which the BIOS-integrated updater does not show (to us. It can report some status codes back to the OS that initiated it. No idea how detailed that error report is though).
The EFI-Updater also handles the PD controllers firmware separately, as those must not restart if the device is standalone, without battery and currently being solely powered through one of those PD controllers. Something, that FW apparently did not account for with the self-updating of the BIOS.
The instability of the EFI-updater seems to stem from the script FW uses to tie the various EFI updates & executables together and how it does not handle all situations. Like when some drive is behaving unexpectedly etc.
But in general, Capsule-Updates are the superior way, because the manufacturer has the most control over what is happening during the upgrade. Only the manufacturer-provided BIOS is running, the user is not involved in setting up a drive with a (minimal) OS on it to run executables that make critical changes to the system. Configurations and modifications to the OS the user could have made are irrelevant when the device is self-updating. But for that the self-updating has to work fully and reliably. Which it obviously does not.